Download Upgrading Your Skills to MCSA: Windows Server 2016.70-743.PracticeTest.2017-07-05.103q.vcex
| Vendor: | Microsoft |
| Exam Code: | 70-743 |
| Exam Name: | Upgrading Your Skills to MCSA: Windows Server 2016 |
| Date: | Jul 05, 2017 |
| File Size: | 19 MB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
Note: This question is part of a series of a questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some questions sets might have more than one correct solutions, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory forest named contoso.com. The forest contains a member server named Server1 that runs Windows Server 2016. All domain controllers run Windows Server 2012 R2.
Contoso.com has the following configuration.

You plan to deploy an Active Directory Federation Services (AD FS) farm on Server1 and to configure device registration.
You need to configure Active Directory to support the planned deployment.
Solution: You upgrade a domain controller to Windows Server 2016.
Does this meet the goal?
- Yes
- No
Correct answer: A
Explanation:
Windows Server 2016 Domain controller is required for Device Registration for Servers that run Windows Server 2016. References: https://technet.microsoft.com/en-us/windows-server-docs/identity/adfs/operations/configure-device-based-conditional-access-on-premises Windows Server 2016 Domain controller is required for Device Registration for Servers that run Windows Server 2016.
References: https://technet.microsoft.com/en-us/windows-server-docs/identity/adfs/operations/configure-device-based-conditional-access-on-premises
Question 2
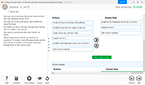
You have a server named Server1 that runs Windows Server 2016. Server1 has the Web Application Proxy role service installed.
You are publishing an application named App1 that will use Integrated Windows authentication as shown in the following graphic.
(Click the Exhibit button.)
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
Correct answer: To work with this question, an Exam Simulator is required.
Explanation:
Publish an Integrated Windows authenticated-based Application for Web Browser Clients Step 1: (configure the Backend server SPN – see first bulleted item below)Before you begin, make sure that you have done the following:* Made sure that the Web Application Proxy servers are configured for delegation to the service principal names (SPN) of the backend servers. * Created a non-claims-aware relying party trust for the application in the AD FS Management console. * Configured the backend server to support Kerberos constrained delegation on the domain controller or by using the Set-ADUser cmdlet with the -PrincipalsAllowedToDelegateToAccount parameter. Note that if the backend server is running on Windows Server 2012 R2 or Windows Server 2012, you can also run this PowerShell command on the backend server. * Verified that a certificate on the Web Application Proxy server is suitable for the application you want to publish. Step 2: http//server2.contoso.com/publish/app1Use the same URL as the backend server URL. Web Application Proxy can translate host names in URLs, but cannot translate path names. Therefore, you can enter different host names, but you must enter the same path name. For example, you can enter an external URL of https://apps.contoso.com/app1/ and a backend server URL of http://app-server/app1/. However, you cannot enter an external URL of https://apps.contoso.com/app1/ and a backend server URL of https://apps.contoso.com/internal-app1/.References: https://technet.microsoft.com/en-us/library/dn383640(v=ws.11).aspx Publish an Integrated Windows authenticated-based Application for Web Browser Clients
Step 1: (configure the Backend server SPN – see first bulleted item below)
Before you begin, make sure that you have done the following:
* Made sure that the Web Application Proxy servers are configured for delegation to the service principal names (SPN) of the backend servers.
* Created a non-claims-aware relying party trust for the application in the AD FS Management console.
* Configured the backend server to support Kerberos constrained delegation on the domain controller or by using the Set-ADUser cmdlet with the -PrincipalsAllowedToDelegateToAccount parameter. Note that if the backend server is running on Windows Server 2012 R2 or Windows Server 2012, you can also run this PowerShell command on the backend server.
* Verified that a certificate on the Web Application Proxy server is suitable for the application you want to publish.
Step 2: http//server2.contoso.com/publish/app1
Use the same URL as the backend server URL.
Web Application Proxy can translate host names in URLs, but cannot translate path names. Therefore, you can enter different host names, but you must enter the same path name. For example, you can enter an external URL of https://apps.contoso.com/app1/ and a backend server URL of http://app-server/app1/. However, you cannot enter an external URL of https://apps.contoso.com/app1/ and a backend server URL of https://apps.contoso.com/internal-app1/.
References: https://technet.microsoft.com/en-us/library/dn383640(v=ws.11).aspx
Question 3
Note: This question is part of a series of a questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some questions sets might have more than one correct solutions, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory forest named contoso.com. The forest contains a member server named Server1 that runs Windows Server 2016. All domain controllers run Windows Server 2012 R2.
Contoso.com has the following configuration.

You plan to deploy an Active Directory Federation Services (AD FS) farm on Server1 and to configure device registration.
You need to configure Active Directory to support the planned deployment.
Solution: You raise the forest functional level to Windows Server 2012 R2.
Does this meet the goal?
- Yes
- No
Correct answer: B
Explanation:
Windows Server 2016 Domain controller is required for Device Registration for Servers that run Windows Server 2016. References: https://technet.microsoft.com/en-us/windows-server-docs/identity/ad-fs/operations/configure-device-based-conditional-access-on-premises Windows Server 2016 Domain controller is required for Device Registration for Servers that run Windows Server 2016.
References: https://technet.microsoft.com/en-us/windows-server-docs/identity/ad-fs/operations/configure-device-based-conditional-access-on-premises
Question 4
You have a server named Server1 that runs Windows Server 2016.
You need to deploy the first cluster node of a Network Controller cluster.
Which four cmdlets should you run in sequence? To answer, move the appropriate cmdlets from the list of cmdlets to the answer area and arrange them in the correct order.
Correct answer: To work with this question, an Exam Simulator is required.
Explanation:
Deploy Network Controller using Windows PowerShell Step 1: Install-WindowsFeatureInstall the Network Controller server role To install Network Controller by using Windows PowerShell, type the following commands at a Windows PowerShell prompt, and then press ENTER. Install-WindowsFeature -Name NetworkController –IncludeManagementTools Step 2: New-NetworkControllerNodeObjectYou can create a Network Controller cluster by creating a node object and then configuring the cluster. You need to create a node object for each computer or VM that is a member of the Network Controller cluster. To create a node object, type the following command at the Windows PowerShell command prompt, and then press ENTER. Ensure that you add values for each parameter that are appropriate for your deployment. New-NetworkControllerNodeObject –Name <string> -Server <String> -FaultDomain <string>-RestInte Step 3: Install-NetworkControllerClusterTo configure the cluster, type the following command at the Windows PowerShell command prompt, and then press ENTER. Ensure that you add values for each parameter that are appropriate for your deployment. Install-NetworkControllerCluster –Node <NetworkControllerNode[]> –ClusterAuthentication … Step 4: Install-NetworkControllerTo configure the Network Controller application, type the following command at the Windows PowerShell command prompt, and then press ENTER. Ensure that you add values for each parameter that are appropriate for your deployment. Install-NetworkController –Node <NetworkControllerNode[]> –ClientAuthentication References: https://technet.microsoft.com/en-us/library/mt282165.aspx Deploy Network Controller using Windows PowerShell
Step 1: Install-WindowsFeature
Install the Network Controller server role
To install Network Controller by using Windows PowerShell, type the following commands at a Windows PowerShell prompt, and then press ENTER.
Install-WindowsFeature -Name NetworkController –IncludeManagementTools
Step 2: New-NetworkControllerNodeObject
You can create a Network Controller cluster by creating a node object and then configuring the cluster.
You need to create a node object for each computer or VM that is a member of the Network Controller cluster.
To create a node object, type the following command at the Windows PowerShell command prompt, and then press ENTER. Ensure that you add values for each parameter that are appropriate for your deployment.
New-NetworkControllerNodeObject –Name <string> -Server <String> -FaultDomain <string>-RestInte
Step 3: Install-NetworkControllerCluster
To configure the cluster, type the following command at the Windows PowerShell command prompt, and then press ENTER. Ensure that you add values for each parameter that are appropriate for your deployment.
Install-NetworkControllerCluster –Node <NetworkControllerNode[]> –ClusterAuthentication …
Step 4: Install-NetworkController
To configure the Network Controller application, type the following command at the Windows PowerShell command prompt, and then press ENTER. Ensure that you add values for each parameter that are appropriate for your deployment.
Install-NetworkController –Node <NetworkControllerNode[]> –ClientAuthentication
References: https://technet.microsoft.com/en-us/library/mt282165.aspx
Question 5
You have an Active Directory domain that contains several Hyper-V hosts that run Windows Server 2016.
You plan to deploy network virtualization and to centrally manage Datacenter Firewall policies.
Which component must you install for the planned deployment?
- the Routing role service
- the Canary Network Diagnostics feature
- the Network Controller server role
- the Data Center Bridging feature
Correct answer: C
Explanation:
Using Windows PowerShell, the REST API, or a management application, you can use Network Controller to manage the following physical and virtual network infrastructure:* Datacenter Firewall This Network Controller feature allows you to configure and manage allow/deny firewall Access Control rules for your workload VMs for both East/West and North/South network traffic in your datacenter. The firewall rules are plumbed in the vSwitch port of workload VMs, and so they are distributed across your workload in the datacenter. Using the Northbound API, you can define the firewall rules for both incoming and outgoing traffic from the workload VM. You can also configure each firewall rule to log the traffic that was allowed or denied by the rule. * Hyper-V VMs and virtual switches * Remote Access Service (RAS) Multitenant Gateways, Virtual Gateways, and gateway pools * Load Balancers References: https://technet.microsoft.com/en-us/library/dn859239.aspx Using Windows PowerShell, the REST API, or a management application, you can use Network Controller to manage the following physical and virtual network infrastructure:
* Datacenter Firewall
This Network Controller feature allows you to configure and manage allow/deny firewall Access Control rules for your workload VMs for both East/West and North/South network traffic in your datacenter. The firewall rules are plumbed in the vSwitch port of workload VMs, and so they are distributed across your workload in the datacenter. Using the Northbound API, you can define the firewall rules for both incoming and outgoing traffic from the workload VM. You can also configure each firewall rule to log the traffic that was allowed or denied by the rule.
* Hyper-V VMs and virtual switches
* Remote Access Service (RAS) Multitenant Gateways, Virtual Gateways, and gateway pools
* Load Balancers
References: https://technet.microsoft.com/en-us/library/dn859239.aspx
Question 6
You have a Hyper-V host named Server1 that runs Windows Server 2016.
Server1 has a virtual machine named VM1. VM1 is configured to run the Docker daemon.
On VM1, you have a container network that uses transparent mode.
You need to ensure that containers that run on VM1 can obtain IP addresses from DHCP.
What should you do?
- On VM1, run docker network connect.
- On Server1, run docker network connect.
- On VM1, run Get-VMNetworkAdapter –VMName VM1 | Set-VMNetworkAdapter –MacAddressSpoofing On.
- On Server1, run Get-VMNetworkAdapter –VMName VM1 | Set-VMNetworkAdapter – MacAddressSpoofing On.
Correct answer: D
Explanation:
If the container host is virtualized, and you wish to use DHCP for IP assignment, you must enable MACAddressSpoofing. PS C:\> Get-VMNetworkAdapter -VMName ContainerHostVM | Set-VMNetworkAdapter -MacAddressSpoofing OnThe command needs to be run on the Hyper-V host. References: https://msdn.microsoft.com/en-us/virtualization/windowscontainers/management/container_networking If the container host is virtualized, and you wish to use DHCP for IP assignment, you must enable MACAddressSpoofing.
PS C:\> Get-VMNetworkAdapter -VMName ContainerHostVM | Set-VMNetworkAdapter -MacAddressSpoofing On
The command needs to be run on the Hyper-V host.
References: https://msdn.microsoft.com/en-us/virtualization/windowscontainers/management/container_networking
Question 7
You have a server named Server1 that runs Windows Server 2016. You install the Docker daemon on Server1.
You need to configure the Docker daemon to accept connections only on TCP port 64500.
What should you do?
- Edit the configuration.json file.
- Run the Set-Service Windows PowerShell cmdlet.
- Edit the daemon.json file.
- Modify the routing table on Server1.
Correct answer: C
Explanation:
Configure Docker with Configuration File The preferred method for configuring the Docker Engine on Windows is using a configuration file. The configuration file can be found at 'c:\ProgramData\docker\config\daemon.json'.Only the desired configuration changes need to be added to the configuration file. For example, this sample configures the Docker Engine to accept incoming connections on port 64500. All other configuration options will use default values. { "hosts": ["tcp://0.0.0.0:64500"]} References: https://msdn.microsoft.com/en-us/virtualization/windowscontainers/docker/configure_docker_daemon Configure Docker with Configuration File
The preferred method for configuring the Docker Engine on Windows is using a configuration file. The configuration file can be found at 'c:\ProgramData\docker\config\daemon.json'.
Only the desired configuration changes need to be added to the configuration file. For example, this sample configures the Docker Engine to accept incoming connections on port 64500. All other configuration options will use default values.
{
"hosts": ["tcp://0.0.0.0:64500"]
}
References: https://msdn.microsoft.com/en-us/virtualization/windowscontainers/docker/configure_docker_daemon
Question 8
You have a failover cluster named Cluster1.
A virtual machine named VM1 is a highly available virtual machine that runs on Cluster1. A custom application named App1 runs on VM1.
You need to configure monitoring on VM1. If App1 adds an error entry to the Application even log, VM1 should be automatically rebooted and moved to another cluster node.
Which tool should you use?
- Resource Monitor
- Failover Cluster Manager
- Server Manager
- Hyper-V Manager
Correct answer: B
Explanation:
Do you have a large number of virtualized workloads in your cluster? Have you been looking for a solution that allows you to detect if any of the virtualized workloads in your cluster are behaving abnormally? Would you like the cluster service to take recovery actions when these workloads are in an unhealthy state? In Windows Server 2012/2016, there is a great new feature, in Failover Clustering called “VM Monitoring”, which does exactly that – it allows you monitor the health state of applications that are running within a virtual machine and then reports that to the host level so that it can take recovery actions. VM Monitoring can be easily configured using the Failover Cluster Manager through the following steps:Right click on the Virtual Machine role on which you want to configure monitoring Select “More Actions” and then the “Configure Monitoring” options You will then see a list of services that can be configured for monitoring using the Failover Cluster Manager. References: https://blogs.msdn.microsoft.com/clustering/2012/04/18/how-to-configure-vm-monitoring-in-windows-server-2012/ Do you have a large number of virtualized workloads in your cluster? Have you been looking for a solution that allows you to detect if any of the virtualized workloads in your cluster are behaving abnormally? Would you like the cluster service to take recovery actions when these workloads are in an unhealthy state? In Windows Server 2012/2016, there is a great new feature, in Failover Clustering called “VM Monitoring”, which does exactly that – it allows you monitor the health state of applications that are running within a virtual machine and then reports that to the host level so that it can take recovery actions.
VM Monitoring can be easily configured using the Failover Cluster Manager through the following steps:
- Right click on the Virtual Machine role on which you want to configure monitoring
- Select “More Actions” and then the “Configure Monitoring” options
- You will then see a list of services that can be configured for monitoring using the Failover Cluster Manager.
References: https://blogs.msdn.microsoft.com/clustering/2012/04/18/how-to-configure-vm-monitoring-in-windows-server-2012/
Question 9
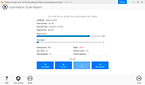
You have a server named Server1 that runs Windows Server 2016.
The disk configuration for Server1 is shown in the exhibit.
(Click the Exhibit button.)
You add Server1 to a cluster.
You need to ensure that you can use Disk 1 for Storage Spaces Direct.
What should you do first?
- Set Disk 1 to offline.
- Convert Partition (E:) to ReFS.
- Convert Disk 1 to a dynamic disk.
- Delete Partition (E:).
Correct answer: D
Explanation:
The disks used in Storage Spaces Direct cannot contain existing partitions. The disks used in Storage Spaces Direct cannot contain existing partitions.
Question 10
Your network contains an Active Directory domain. The domain contains two Hyper-V hosts.
You plan to perform live migrations between the hosts.
You need to ensure that the live migration traffic is authenticated by using Kerberos.
What should you do first?
- From Server Manager, install the Host Guardian Service server role on a domain controller.
- From Active Directory Users and Computers, add the computer accounts for both servers to the Cryptographic Operators group.
- From Active Directory Users and Computers, modify the Delegation properties of the computer accounts for both servers.
- From Server Manager, install the Host Guardian Service server role on both servers.
Correct answer: C
Explanation:
If you have decided to use Kerberos to authenticate live migration traffic, configure constrained delegation before you proceed to the rest of the steps. To configure constrained delegation Open the Active Directory Users and Computers snap-in. From the navigation pane, select the domain and double-click the Computers folder. From the Computers folder, right-click the computer account of the source server and then click Properties. In the Properties dialog box, click the Delegation tab. On the delegation tab, select Trust this computer for delegation to the specified services only. Under that option, select Use Kerberos only. If you have decided to use Kerberos to authenticate live migration traffic, configure constrained delegation before you proceed to the rest of the steps.
To configure constrained delegation
- Open the Active Directory Users and Computers snap-in.
- From the navigation pane, select the domain and double-click the Computers folder.
- From the Computers folder, right-click the computer account of the source server and then click Properties.
- In the Properties dialog box, click the Delegation tab.
- On the delegation tab, select Trust this computer for delegation to the specified services only. Under that option, select Use Kerberos only.
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files
HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files
ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!